- Dev Shack Academy
- Posts
- Don't leak your env variables in Cursor
Don't leak your env variables in Cursor
Avoid this one mistake that could expose your sensitive API keys
It’s an exciting time to be a developer.
AI and Large Language Models (LLMs) are improving at breakneck speeds.
This really gives developers incredible tools to build faster and be more productive.(who wants to write regex expressions manually anyway).
The ability to build at speed and in a smarter way is exciting to watch unfold. As we implement new kinds of tools into our development tool-chains, we must watch out for potential pitfalls that might arise.
This is not a AI dooms-day post.
Instead, it’s a quick heads up about a security related issue I spotted when working with a new IDE Cursor.
Experimenting with Cursor
I’ve been experimenting with an IDE called Cursor. It’s an amazing product, and hats off to the cursor team for creating it.
For those who haven’t used it, it basically extends visual studio’s IDE capabilities by overlaying the normal IDE with enhanced Gen-AI coding capabilities.
It even has an “agent mode“, which allows you to input natural language commands like:
“Scaffold out a new API route and service layer based on this mongoDB schema (highlighted schema code from your IDE). Make sure it conforms to the code style in Example.ts file.“
It kick’s off an agent that will begin writing the new files, implementing the code, while you sit back and watch it all happen.
Pretty neat!
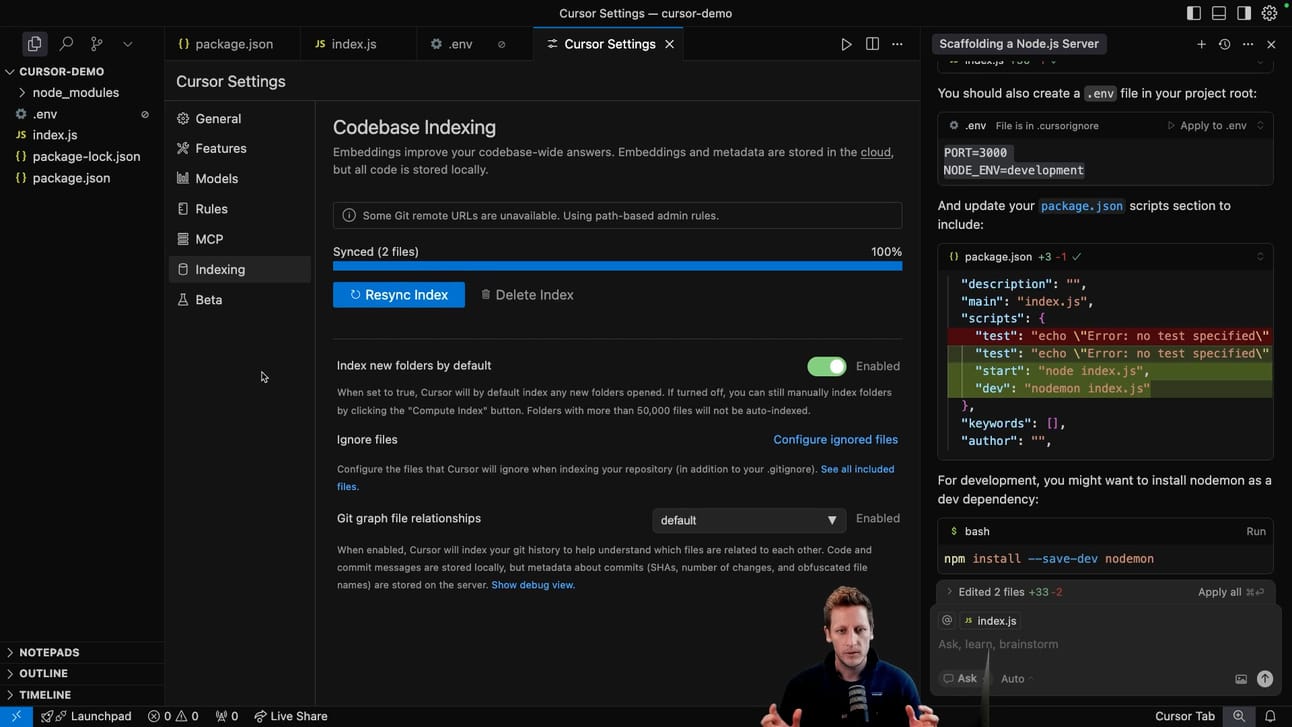
Codebase Indexing
In order for all this to work properly, Cursor has an option in it’s config called indexing, which is enabled by default.
Indexing helps Cursor understand your entire codebase context, which allows smarter suggestions and improves the output of your requests.
Cursor allows you to semantically index your codebase, which allows it to answer questions with the context of all of your code as well as write better code by referencing existing implementations. Codebase indexing is enabled by default, but can be turned off in settings.
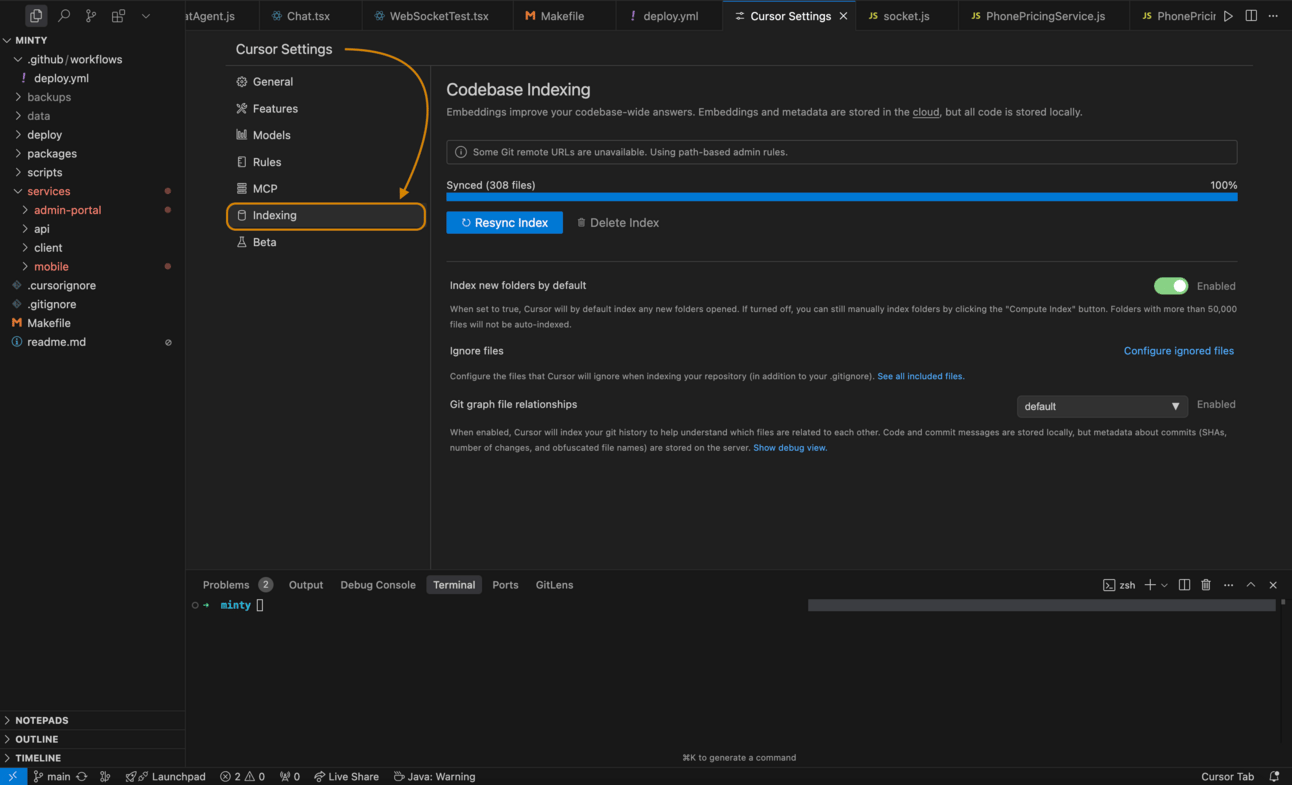
In cursor settings, there is a sub tab called “indexing“.
A quick overview of what is happening under the hood, if indexing is enabled:
Cursor scans through your codebase and breaks it up into smaller pieces (this is called chunking).
It then stores these chunks as embeddings in a vector store in the cloud.
When you ask a question locally, it computes an embedding of your question.
It sends a search to the vector store to find the relevant chunks.
The client will then match the local code using the chunks that are returned from the search.
Cursor will then only send those specific chunks up to the server for context along with your question.
The server will respond with a response to the client.
So what’s the point?
If you have any files that contain sensitive data, or secrets in your project folder, and it isn’t excluded properly using the .cursorignore file, your api keys or client sensitive data my be inadvertently be uploaded and stored to Cursor’s servers.
Not ideal! How do we avoid this? Checkout the video and details below…